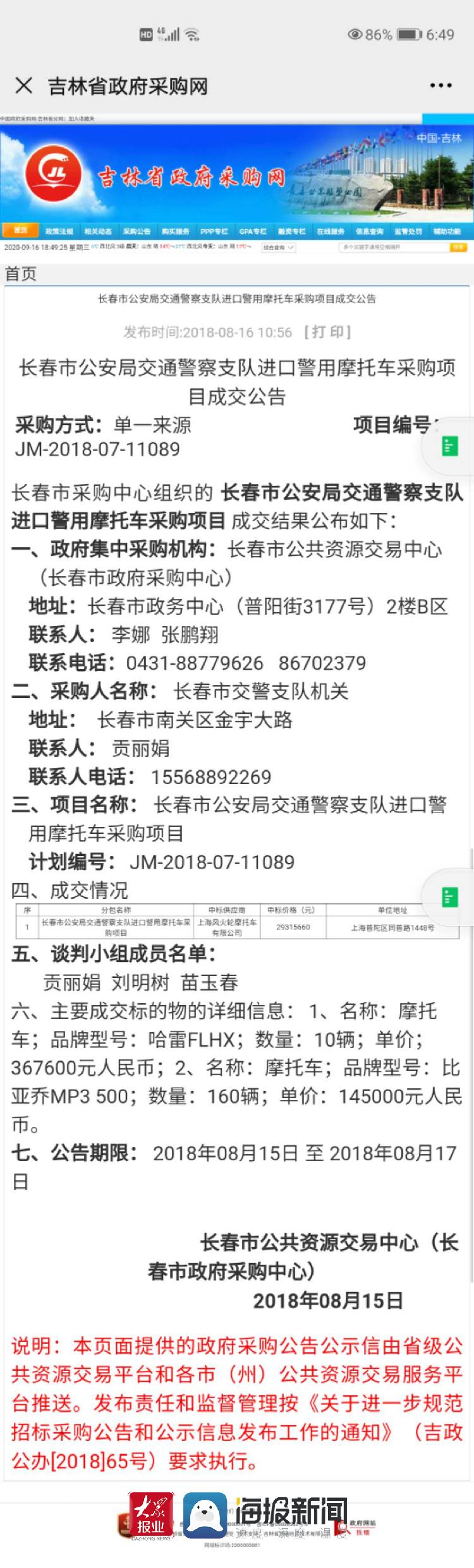
жҖҺж ·зңӢеҫ…жңҖиҝ‘зҲҶеҮәзҡ„ IE е…ЁзүҲжң¬жү§иЎҢжјҸжҙһпјҲCVE-2014-6332пјү
иҪ¬иҪҪдёҖзҜҮ IBM X-Force Researcher Finds Significant Vulnerability in Microsoft WindowsThe IBM X-Force Research team has identified a significant data manipulation vulnerability (CVE-2014-6332) with a CVSS score of 9.3 in every version of Microsoft Windows from Windows 95 onward.
We reported this issue with a working proof-of-concept exploit back in May 2014, and today, Microsoft is patching it. It can be exploited remotely since Microsoft Internet Explorer (IE) 3.0. This complex vulnerability is a rare, вҖңunicorn-likeвҖқ bug found in code that IE relies on but doesnвҖҷt necessarily belong to. The bug can be used by an attacker for drive-by attacks to reliably run code remotely and take over the userвҖҷs machine вҖ” even sidestepping the Enhanced Protected Mode (EPM) sandbox in IE 11 as well as the highly regarded Enhanced Mitigation Experience Toolkit (EMET) anti-exploitation tool Microsoft offers for free.
What Does This Mean?First, this means that significant vulnerabilities can go undetected for some time. In this case, the buggy code is at least 19 years old and has been remotely exploitable for the past 18 years. Looking at the original release code of Windows 95, the problem is present. With the release of IE 3.0, remote exploitation became possible because it introduced Visual Basic Script (VBScript). Other applications over the years may have used the buggy code, though the inclusion of VBScript in IE 3.0 makes it the most likely candidate for an attacker. In some respects, this vulnerability has been sitting in plain sight for a long time despite many other bugs being discovered and patched in the same Windows library (OleAut32).
Second, it indicates that there may be other bugs still to be discovered that relate more to arbitrary data manipulation than more conventional vulnerabilities such as buffer overflows and use-after-free issues. These data manipulation vulnerabilities could lead to substantial exploitation scenarios from the manipulation of data values to remote code execution. In fact, there may be multiple exploitation techniques that lead to possible remote code execution, as is the case with this particular bug. Typically, attackers use remote code execution to install malware, which may have any number of malicious actions, such as keylogging, screen-grabbing and remote access.
IBM X-Force has had product coverage with its network intrusion prevention system (IPS) since reporting this vulnerability back in May 2014, though X-Force hasnвҖҷt found any evidence of exploitation of this particular bug in the wild. I have no doubt that it would have fetched six figures on the gray market. The proof of concept IBM X-Force built uses a technique that other people have discovered, too. In fact, it was presented at this yearвҖҷs Black Hat USA Conference.
Technical DescriptionIn VBScript, array elements are actually Component Object Model (COM) SafeArrays. Each element is a fixed size of 16 bytes, with an initial WORD indicating the Variant type. Under normal circumstances, one will only have control of a maximum of 8 bytes of this data through either the Variant type for double values or for currency values.
жҺЁиҚҗйҳ…иҜ»
- иҒӘжҳҺдәәе…»иҠұпјҢиҝҷ3з§ҚвҖңиҠұвҖқжҖҺж ·д№ҹиҰҒе…»дёҖзӣҶпјҢжҜҸе№ҙиғҪзңҒдёҚе°‘еҢ»иҚҜиҙ№
- иҝ‘400е№ҙжқҘжңЁжҳҹеңҹжҳҹзӣёи·қжңҖиҝ‘еҗ„ең°еҸҜи§ҒиҝҷдёҖзҪ•и§ҒеҘҮи§Ӯ
- жңҖиҝ‘зңӢеҲ°еҫҲеӨҡеҫ®йӮҰе…Ӣзҡ„е®Јдј пјҢеҸҜдҝЎеҗ—пјҢе’Ңеҫ®дј—银иЎҢе•Ҙе…ізі»е•Ҡ
- дә’иҒ”зҪ‘жҖҺж ·и§ЈеҶівҖң家ж”ҝжңҚеҠЎдёҠй—ЁйҖҹеәҰж…ўвҖқзҡ„й—®йўҳ
- жҖҺж ·зңӢеҫ…д»Һ1жңҲ8еҸ·иө·пјҢQQй’ұеҢ…ејҖе§ӢжҸҗзҺ°ж”¶иҙ№
- 银иЎҢitдәәжҖҺж ·иҪ¬еһӢ
- жұҪиҪҰ|еҶ¬еӨ©жҖҺж ·и®©иҪҰеҶ…жё©еәҰеҝ«йҖҹеҚҮй«ҳпјҹеә§жӨ…еҠ зғӯзҡ„жңҖдҪідҪҝз”Ёж–№ејҸдәҢпјҢеӨ–еҫӘзҺҜзҡ„дҪңз”ЁжҖ»з»“
- жҖҺж ·иҝӣе…ҘйҖҡдҝЎиЎҢдёҡ
- жҖҺж ·иҜ„д»·жү¶д»–жҹ жӘ¬иҢ¶зҡ„е°ҸиҜҙгҖҠдә‘е…»жұүгҖӢзҡ„з»“е°ҫ
- жҖҺж ·жҲҗдёәдёҖеҗҚеҗҲж јзҡ„PythonзЁӢеәҸе‘ҳ?